The "game.droid" file holds a secret. If you search for the PNG header (89 50 4E 47 0D 0A 1A 0A) you will find it twice. If you search for the PNG terminator (49 45 4E 44 AE 42 60 82 00) you will find it twice.
Conclusion: there are two hidden PNGs inside this game.droid file.
Extracting them out yields these two images. Is this what you're looking for?
First image:
![[Image: u6MbvE5.png]](https://i.imgur.com/u6MbvE5.png)
Second image (white on transparent background, you might not see it in this web view as well as in say photoshop):
![[Image: UCXuqhp.png]](https://i.imgur.com/UCXuqhp.png)
EDIT: There appears to be a noticable bleed area around the sprites. The creator of the game has used a postprocessor to "pack" these sprites as tight as possible to a single "texture atlas" and set a bleed setting to two pixels. See image below:
![[Image: gzSkoTd.png]](https://i.imgur.com/gzSkoTd.png)
This means that the game, when running, must have a lookup table of all the XYWHs somewhere. Did some searching and they are intact. I will update this post soon.
EDIT: I see now. At 0x73214 there begins an array where each entry is 22 bytes long. One entry defines where the sprite is in the atlas, its size, its hitbox size and something unknown. It's a matter of reading 22 bytes at a time from 0x73214 onwards as eleven unsigned little endian shorts: X Y W H I I I I I I I (I is for Ignore)
Just eyeballing it, looks like there's 0x8694 bytes, so 0x8694/0x16 = 0x61E == 1566 sprites. I am now writing a "cookie cutter" script.
EDIT: I was wrong, there's 1562 sprites. I extracted them now (sorry, no names!) and they're here:
https://www.dropbox.com/s/86wgytn3pwuqb9...1.zip?dl=0



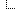


![[Image: u6MbvE5.png]](https://i.imgur.com/u6MbvE5.png)
![[Image: UCXuqhp.png]](https://i.imgur.com/UCXuqhp.png)
![[Image: gzSkoTd.png]](https://i.imgur.com/gzSkoTd.png)