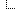05-20-2021, 12:47 AM
(This post was last modified: 05-20-2021, 01:16 AM by Videogamer555.)
(05-19-2021, 03:01 AM)DatOneTaiwanGuy Wrote: The set of files from the server, and they normally start with the manifest file that's not encrypted, the abconfig file for the assets from the manifest file that automatically decrypts for the game in the memory, the criware assets, other designs in .bin format and one json file.
That's how it starts.
I don't have a way of intercepting the communications between the game and its server, but I do have a way of dumping all the files after they have been downloaded. I ran BlueStacks emulator and played the game until it did its 900MB download, to get all its files. Then I copied the files from BlueStacks file system, using another program, which is based on the ADB program from the Android SDK. In so doing, I managed to copy all the game's downloaded files from inside BlueStacks over to my actual OS, where I can access them normally via Windows Explorer. But I have a problem with them. They are given file names that have no file extension, and who's names are hexadecimal-digit strings that appear to be either some kind of hash or the UUIDs for the files. Here's a screenshot showing some of the file names.
![[Image: Ndc9aci.png]](https://i.imgur.com/Ndc9aci.png)
And I don't know what any of the files are supposed to be. It would help if I knew what the contents of the files should be, so that when I tried to decrypt them I would know if they had been successfully decrypted. By the way, here's a screenshot showing the first 912 bytes of the first of these encrypted files in a hex editor. Is this what it should look like before decryption?
![[Image: 0VBmv3v.png]](https://i.imgur.com/0VBmv3v.png)
By the way, is the decryption supposed to start with the first byte in the file, or at some offset into the file? In other words, is the entire file encrypted, or only part of it? Also, how will I know which of the above decryption keys mentioned is actually the correct one? The XOR keys cycle at different rates, based on their length, and the number of 0x00 bytes at the end sets their length.
By the way, is the encryption just simple XOR where the key's bytes repeat over and over again and are XORed into the data? Or is it RC4, which using a certain random number generator which is initialized by the key, and the bytes output from that random number generator are XORed into the data?